September 22, 2012
Google Destroying Blogspot?
or just making my life more difficult. We blogspotters have been forced onto an interface that looks more like Wordpress, which as far as I can tell is clunkier and gives us less control. I've considered migrating to Wordpress before – I could host my blogs on my own server and have greater privacy, etc. – but rejected it because the blogspot user interface was superior. Google has chosen to trash that advantage.
Testing image control and positioning with the image right.
Ok, maybe I can get used to this, but where the h*ll do I enter labels?
August 6, 2012
Wozniak: Cloud Computing Will Cause "Horrible Problems"
 "Wozniak didn't offer much in the way of specifics . . . . [but said, 't]he more we transfer everything onto the web, onto the cloud, the less we're going to have control over it.'" Steve Wozniak was the inventor of the Apple I and Apple II computers.
"Wozniak didn't offer much in the way of specifics . . . . [but said, 't]he more we transfer everything onto the web, onto the cloud, the less we're going to have control over it.'" Steve Wozniak was the inventor of the Apple I and Apple II computers.
More at Business Insider. You can find more re- the kinds of problems I worry about by clicking on the label, "Worldbeam," at the bottom of this post.
July 21, 2012
A Few Headlines: Facebook & Other Big Bros., & the Nasher v. Museum Tower
 More at the links.
More at the links.
1. What Facebook Knows. "[O]n 219 million randomly chosen occasions, Facebook prevented someone from seeing a link shared by a friend. Hiding links this way created a control group . . . . the company is not above using its platform to tweak users' behavior. . . . By learning more about how small changes on Facebook can alter users' behavior outside the site, the company eventually 'could allow others to make use of Facebook in the same way' says Marlow."
(Rough translation of image at left: "I give the secrets of big companies to you, and I am a terrorist – Assange; I give your secrets to big companies, and I am Man of the Year – Zuckerberg.")
2. Three NSA Whistleblowers Back EFF's Lawsuit Re- Gov't's Massive Spying on US Civilians. "Three . . . former employees of the National Security Agency (NSA) . . . have come forward to . . . confirm that the NSA has, or is in the process of obtaining, the capability to seize and store most electronic communications passing through its U.S. intercept centers, such as the 'secret room' at the AT&T facility in San Francisco first disclosed by retired AT&T technician Mark Klein in early 2006." (Link added.)
3. US Nat'l Reconnaissance Office's Castoff 'Scopes Beat NASA's Hubbell. "The U.S. government’s secret space program has decided to give NASA two telescopes . . . . [d]esigned for surveillance [and] no longer needed for spy missions . . . . These telescopes will have 100 times the field of view of the Hubble . . . . NASA official Michael Moore gave some hint of what a Hubble-class space telescope might do if used for national security: 'With a Hubble here you could see a dime sitting on top of the Washington Monument.'"
 4. A Modest Proposal. In case you missed it, Dallas's latest addition to housing for the 1%, Museum Tower, is frying everything within its line of sight on the Nasher Museum premises. "So [writes Christina Rees in Glasstire], one of Dallas’s more admirable enfant terribles, Erik Schuessler . . . came up with an early solution, and so far I haven’t seen one to beat it." (Link added; click on the images for larger versions.)
4. A Modest Proposal. In case you missed it, Dallas's latest addition to housing for the 1%, Museum Tower, is frying everything within its line of sight on the Nasher Museum premises. "So [writes Christina Rees in Glasstire], one of Dallas’s more admirable enfant terribles, Erik Schuessler . . . came up with an early solution, and so far I haven’t seen one to beat it." (Link added; click on the images for larger versions.)
February 20, 2012
Transparency Grenade
 "The device is essentially a small computer with a powerful wireless antenna and a microphone. Following detonation, the grenade intercepts local network traffic and captures audio data, then makes the information immediately available online. . . . The grenade form factor may be a great vehicle for artistic expression, but its conspicuous nature makes it slightly impractical – and could see you propelled face first into the pavement by a member of law enforcement. That's why the development of an application for rooted Android devices is already under way. Constantly running in the background on a smartphone, the transparency grenade app is going to provide some of the original device's functionality."
"The device is essentially a small computer with a powerful wireless antenna and a microphone. Following detonation, the grenade intercepts local network traffic and captures audio data, then makes the information immediately available online. . . . The grenade form factor may be a great vehicle for artistic expression, but its conspicuous nature makes it slightly impractical – and could see you propelled face first into the pavement by a member of law enforcement. That's why the development of an application for rooted Android devices is already under way. Constantly running in the background on a smartphone, the transparency grenade app is going to provide some of the original device's functionality."
Designed by Julian Oliver, with metal parts crafted by Susanne Stauch. The development process is funded by donations. See transparencygrenade for more info, including how to donate.
July 6, 2011
The Hacker Ethic
 I've been reading Hackers by Steven Levy (1984, 1994); 25th Anniversary edition here. The book recounts the seminal exploits of a relatively small number of nerds who, during the late 1950s through the early '80s, created the basic architecture of computer cognition and memory that we inhabit today.
I've been reading Hackers by Steven Levy (1984, 1994); 25th Anniversary edition here. The book recounts the seminal exploits of a relatively small number of nerds who, during the late 1950s through the early '80s, created the basic architecture of computer cognition and memory that we inhabit today.
The meaning of the term, "hacker," has been hijacked since Levy's first edition was published. Now, it's used to suggest a cyber-burglar or worse, who steals or vandalizes for her/his personal profit or pleasure.
But originally, the term simply referred to one who creates computer hardware or software. Levy's "hackers" wrote the operating systems and visual interfaces that brought the mammoth, early computers under our recreative as well as productive control and developed the first widely-available personal computers, among other accomplishments.
And as the Amazon "product description" adds, "[t]hey had a shared sense of values, known as 'the hacker ethic,' that still thrives today."
The "hacker ethic":
- Access to computers – and anything that might teach you something about the way the world works – should be unlimited and total.
- All information should be free.
- Mistrust authority; promote decentralization.
- Hackers should be judged by their hacking, not bogus criteria such as degrees, age, race, or position.
- You can create art and beauty on a computer.
- Computers can change your life for the better.
(See Hackers by Steven Levy, p. 34 {2010 O'Reilly Media, Kindle Edition}.)
For years, these hackers worked day and night, driven by the sheer joy of creating something really cool, and receiving little or nothing more for their efforts beyond the respect of their few, similarly-obsessed fellows. They freely shared the programs and equipment they created, each helping the others to improve and de-bug their creations. As far as they were concerned, none of it should be owned, so none of it could be stolen.
The hackers inhabited a sort of cyber-utopian anarchy in which the only abuse that occurred consisted in the wrong-headed efforts of bureaucrats to restrict access based on claims such as a need for "security." And it was the hacker ethic that made possible the incredible flowering of human potential that occurred during this first decade or two leading up to the commercial success of personal computers and p.c.-based video games.
For me, the fact that such a benevolent anarchy can and has in fact endured for an extended period was one of many interesting revelations afforded by this book. It also provides what seems to be a conscientiously compiled history of our subsequent fall from this Eden, as well as a wealth of details about key, individual hackers and their deeds.
I read the paperback and then bought the e-book; recommended as an invaluable resource.
I recently came across an interesting site, datalove, propounding similar principles:
Data is essentialDatalove appears to be affiliated with Telecomix, one of the Anonymous-type organizations involved in efforts to help Egyptian protesters circumvent Mubarek's shut-down of the Egyptian internet.
Data must flow
Data must be used
Data is neither good nor bad
There is no illegal data
Data is free
Data cannot be owned
No man, machine or system shall interrupt the flow of data
Locking data is a crime against datanity
Love data
One of the nerds described in Levy's Hackers was John Conway, who created the computer game of Life, in which the goal is to design simple, graphic life-forms and then observe how their community either dies out or achieves immortality; below are gifs showing two "immortal" results from this game: (1) a single Gosper's Glider Gun creating "gliders" and (2) a breeder that leaves glider guns in its wake:
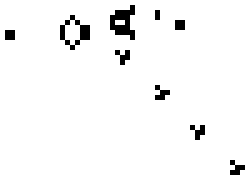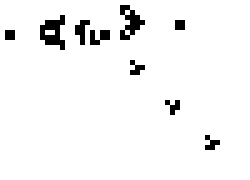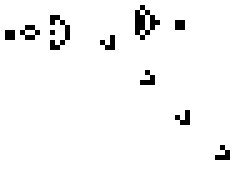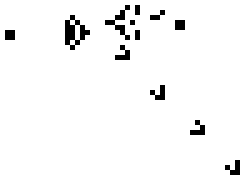
August 30, 2010
Free Phone via Google Vs. --?
 As reported rather breathlessly by The NYT, you can now make and receive phone calls to/from regular phones from/at your computer for free, without using iChat or Skype, although you have to set up Gmail and Google Voice accounts to do it. This is "a big deal" because:
As reported rather breathlessly by The NYT, you can now make and receive phone calls to/from regular phones from/at your computer for free, without using iChat or Skype, although you have to set up Gmail and Google Voice accounts to do it. This is "a big deal" because:
The ultimate, of course, would be free calls from a phone, to a phone. But until now, all we’ve been able to do is dance around that concept.Of course, some of us might actually still be willing to purchase our phone services from AT&T et al. in exchange for greater privacy. But then, they'd have to provide privacy.
For example, chat programs let you make free calls, computer-to-computer. Skype lets you make free calls from your cellphone, but not to regular phone numbers. Skype and Line2 let you make calls from your cellphone (when you’re in a 3G area or on Wi-Fi), to actual phone numbers — but not free.
What Voice Calls from Gmail does is open up another variation, one that [enables free] calls “from a computer, to a phone.” . . . What if Google released an app like that for Android phones, or the iPhone? . . . At that point, you could, for the first time in history, make unlimited free phone-to-phone calls.
. . . That development would cause conniptions at the cellphone companies, that’s for sure."
January 6, 2009
Update on Bringing the Internets to Heel
"Comcast's bandwidth throttling system that slows you down for using too much bandwidth is now fully armed and operational in all markets. Here's how it works, and how to not get stuck on the short bus." More at Gizmodo. (Thanks, Ben!)
December 28, 2008
UPDATE: Ending the Internet as We've Known It
Sorry to keep pounding this but I can't believe how many people still don't get it.
Via Slashdot,
"Microsoft's vision of your computing future is on display in its just-published patent application for the Metered Pay-As-You-Go Computing Experience. The plan, as Microsoft explains it, involves charging students $1.15 an hour to do their homework, making an Office bundle available for $1/hour, and billing gamers $1.25 for each hour of fun. In addition to your PC, Microsoft also discloses plans to bring the chargeback scheme to your cellphone and automobile — GPS, satellite radio, backseat video entertainment system. 'Both users and suppliers benefit from this new business model,' concludes Microsoft, while conceding that 'the supplier can develop a revenue stream business that may actually have higher value than the one-time purchase model currently practiced.' But don't worry kids, that's only if you do more than 52 hours of homework a year!"This is an important step in the devolution I've outlined in previous posts that's transforming the internets as we've known them into something controlled centrally from the top down by mega-corps and gummints. I realize that that transformation could yield efficiencies in some areas, but I think they'll mainly benefit the controllers (them), not the controllees (us).
My main concerns relate to the power of those who own or control the more centralized system, which power will be enormously enhanced to do any or all of the following:
(1) To charge us whatever they like for their services, including but not limited to forcing us to pay for and use upgrades that we don't want or that are incompatible with older documents or software that we still want to use;As I said in my 6/3/07 post, "effective regulation or oversight over those in possession of that ownership and control [of the devolved system] would become impossible, since they would have the power with a few keystrokes to alter every digital record on the planet . . . ."
(2) To surveille us without any "probable cause" to suspect us of wrongdoing, in violation of the U.S. Constitution, esp. the Fourth Amendment; and
(3) To alter or delete any information or data, whether accidentally or intentionally, if they consider it a "threat" or simply inconsistent with their own interests.
The following is from my 10/3/07 post on the subject:
Free speech in general and the internet in particular seem to worry control freaks.(There's a "Search Blog" function at upper left on this page; you can enter "internet" or other terms to find additional, related posts.)
As of 2000, just five megacorporations – Time Warner, Disney, Murdoch's News Corporation, Bertelsmann of Germany, and Viacom (formerly CBS) – controlled over 90% of the media industry in the U.S., with General Electric's NBC a close sixth (see here, here, here, and here).
In 2003, despite the largest public outcry in FCC history, the FCC adopted rules loosening restrictions on media ownership (stories here, here, and here) . . . .
Certain people have spent a lot of money to gain all that control, and notwithstanding claims of hard times in the media biz, the investment has in fact proved profitable; but one of the main benefits that might have been hoped for – control over the agenda and messages reaching audiences of any significant size – is threatened by the 'net.
* * * * *
In an earlier post, I discussed conservatives' plans to replace the internet as we know it with something called the "Worldbeam" (a.k.a. the "Cloud"), a system in which, instead of storing all your personal docs, files, and software on your own computer at home, everything would be stored on larger computers elsewhere, and you would just have a box that would be little more than a gateway to the Beam.
Instead of buying your own copies of applications, the most basic might (or might not) be provided on the Beam for free, and you'd pay license fees for anything fancy, so vendors could force you to upgrade whenever they liked. Although access to your own data would theoretically be protected by a password or other security, the gummint or others who controlled the Beam could access, modify, or simply delete any or all of your or others' data much more easily than now.
The internet would have been transformed into a massive, top-down surveillance system while conferring virtually unlimited power on those who controlled it to re-write "reality." [As I said in my 6/3/07 post, "[w]ho controls the Beam will control history, and thus will have the power to botch if not completely control the present and future."]
I was worried, but thought it would be some years before the "Beam" replaced the 'net as we know it.
Duh. It's finally dawned on me, there's no need for those desiring Beam-like control to engineer any single, vast switch-over to a new system. They're simply colonizing the 'net little by little – and many of us are unwittingly helping them.
Think MySpace, Facebook, Flickr, MeetUp, LinkedIn, del.icio.us, Ancestry.com, and yes, Blogspot – you upload or create tons of data about yourself and your activities, opinions, social and other relationships, and personal preferences into online facilities that are maintained and controlled by other people. You may or may not even keep copies on your own computer of everything you put on the 'net. Think online banking and investment, every airplane ticket you've ever bought and hotel you've booked, every comment you've ever posted, and every purchase you've ever made esp. from vendors like amazon that keep track so as to make recommendations. Think on-line spam filter services (I realize AT&T is probably already giving the gummint copies of every e-mail that passes through AT&T's "pipes," in direct violation of our constitutional rights -- see here [and here, here, here, and here] -- but hey, we managed to shut that down, didn't we? Oops, guess not [link supplied].) . . .
* * * * *
At least now, of course, we CAN keep copies of our stuff on our own computers. My computer can of course be infected or hacked; but I can fight that in various ways that at least make it more difficult for my privacy etc. to be massively violated by the gummint, etc. Theoretically, I could even put stuff on a computer that has no wireless port and isn't otherwise connected to the 'net, so someone would have to have actual physical access to it in order to alter or delete it [and if you are an activist who opposes gummint policies, I recommend you do this].
As I look back at what I've posted before, the only thing that's changed is that the devolution is happening even more quickly than I imagined possible.
As I also said in my 6/3/07 post, "I happen to agree that all information is good information. But what needs to be spelled out in no uncertain terms is that because knowledge is power, a balance of power requires a balance of knowledge." Right now, the powerful know a lot more about us than we know about them; that needs to change.
December 6, 2008
The Death of YouTube as We've Known It?
As reported by ipower, "As of yesterday YouTube has replaced its list of 'Most Viewed' videos on the site's 'Videos' section with a varied selection of sponsor-friendly videos that the site calls 'Most Popular'. Where users normally see videos with high view-counts that have become popular due to viral spreading and community activity, we now see videos like the new MacBook commercial that gets showcased on the 'Most Popular' #1 spot while having very low view-counts and even lower ratings. YouTube will no longer give massive exposure to its community's video productions and instead is now tightly controlling its Videos pages to attract more sponsors and a more mainstream audience." More at the link above.
August 12, 2008
iPatriot Act Ready and Waiting for i911; and, About the Cloud . . . .
Too impt. not to re-blog. Transcript from starting around 4:30 min.:
Lawrence Lessig: "There's going to be an i-911 event . . . I had dinner once with Richard Clark at the table and I said, 'is there an equivalent to the Patriot Act -- an iPatriot Act -- just sitting waiting for some substantial event . . . for them to come have the excuse for radically changing the way the Internet works?' And he said, 'Of course there is' -- and I swear this is what he said, and quote -- 'and Vint Cerf is not going to like it very much.'"
I wish more people were aware that this is what's been going on; but to quote some useful cliches, nature abhors a vacuum, and the unconscious does not hear the negative. So, it's not enough for us to just point this out and say, we can't let that happen. We need to have our OWN counter-iPatriot proposal sitting on the shelf. Theirs is ready; we'd better catch up fast.
And how about us having a few initiatives of our own that are actually in advance of theirs, instead of merely trying to catch up all the time?
About the Cloud, here's a recent article showing how one of the risks I've discussed has materialized:
"Can you trust your data to the cloud? For users of an online storage service called The Linkup, formerly known as MediaMax, the answer turned out to be a resounding 'no.'The Linkup says 55% of the data is safe, but they're not sure about the other 45%."The Linkup shut down on Aug. 8 after losing access to unspecified amounts of customer data . . . ."
Here's my related, 2007 post.
May 9, 2008
Banksy's New, Biggest Work Yet --
 commenting on CCTV, right under not just their noses, but their cameras:
commenting on CCTV, right under not just their noses, but their cameras:
"The secretive graffiti artist managed to erect three storeys of scaffolding behind a security fence despite being watched by a CCTV camera.
"Then, during darkness and hidden behind a sheet of polythene, he painted this comment on 'Big Brother' society.
* * *
"The work, above a Post Office yard in Newman Street near Oxford Circus, shows a small boy, watched by a security guard, painting the words: 'One nation under CCTV.'"
More here.
March 8, 2008
All Air Passengers to Be Fingerprinted
 According to the U.K.'s Telegraph, all international and domestic passengers leaving Terminal 5 of London's Heathrow Airport will soon be subjected to mandatory fingerprinting. The biometric check is also scheduled to be introduced at other London terminals.
According to the U.K.'s Telegraph, all international and domestic passengers leaving Terminal 5 of London's Heathrow Airport will soon be subjected to mandatory fingerprinting. The biometric check is also scheduled to be introduced at other London terminals."Dr. Gus Hosein, of the London School of Economics, [said,] '[t]here is no other country in the world that requires passengers travelling on internal flights to be fingerprinted. BAA says the fingerprint data will be destroyed, but the records of who has travelled within the country will not be, and it will provide a rich source of data for the police and intelligence agencies.
"'I grew up in a society where you only fingerprinted people if you suspected them of being criminals. . . . There will also be a suspicion that this is the thin end of the wedge, that we are being softened up by making fingerprinting seem normal in the run-up to things like ID cards.'
"Simon Davies, of campaign group Privacy International, [said,] ' . . . the experience in the US has shown that the information can only be used retrospectively, not in real time, as it takes so long to match a fingerprint to the one held on the database. I think once again we are seeing the introduction of technology whose benefits are illusory.'"
Related post here ("Big Brother Has Biometric Data on You").
UPDATE: A British company called ThruVision has developed a camera that can see through clothing to reveal what's in or under people's pockets from 80 feet away. It's called the T5000, and detects different materials based on the different signatures of Terahertz waves, or "T-rays," they emit. More at Gizmodo.
February 11, 2008
WaPo: U.S. Border Agents Seizing Laptops, Phones and Copying Info
The Washington Post reports that federal agents at U.S. borders have been seizing and copying the contents of some travellers' laptops, cellphones, and other electronic devices.
The Association of Corporate Travel Executives has tracked complaints from members whose laptops were seized without warrants and without any crime ever being charged. The laptops were usually returned days later, but one member's laptop has yet to be returned after more than a year.
At least two global corporations have directed their executives not to carry confidential business material on laptops overseas. One law firm has instructed its lawyers crossing U.S. borders to carry only "blank laptops," preferring the risks of having their docs hacked while accessing them over the internet to the risks of government search and seizure.
The Electronic Frontier Foundation and other organizations plan to sue to force the government to disclose its policies on border searches, including which rules govern the seizing and copying of the contents of electronic devices.
B.t.w., on the corporate surveillance side, when I accessed the WaPo article, the company or its associates wanted to set 22 cookies. For now, I'm denying all that appear to be not so much for my benefit as for someone else's, which appears to be at least 95% of them.
January 16, 2008
AT&T Considering Monitoring All Internet Traffic
Mind-bogglingly bizarre: per Slate.com, "last week AT&T announced that it is seriously considering plans to examine all the traffic it carries for potential violations of U.S. intellectual property laws. The prospect of AT&T, already accused of spying on our telephone calls, now scanning every e-mail and download for outlawed content is way too totalitarian for my tastes." I'm not sure why they'd bother, if that were the only motivation; sounds more like they're floating an after-the-fact rationalization for Mark Klein's allegations.
December 31, 2007
December 29, 2007
UPDATE Re- Bringing the Internet to Heel
As my three readers know, I'm very concerned that, at least partly through the instigation of right-wing authoritarians but also partly through the more or less semi-witless facilitation by the rest of us, the internet is rapidly being transformed into a potential top-down surveillance and mind-control system easily manipulated by gummints and corps (for more details, see my previous posts on the subject, most recently here).
I never thought I'd see Microsoft as on my side, but in its current battles with Google, that's how it's shaping up. Google is actively promoting its "cloud" model of the internet, in which not only software but most of your data live on the 'net -- i.e., in hardware owned and controlled by others -- while Microsoft continues to favor a distributed model in which most of your software and data live in your PC.
Details at Google Watch and The New York Times, among other places.
Personally, I'm hanging on to my hardware and (better late than never) minimizing the personal info I put on the 'net.
(See my prior post for background.)
December 12, 2007
Do this -- IF You Can Falsify All Your Data
and assuming you're inexplicably desperate to graft yourself into the MS "Borg": Microsoft Offers Free Software in Exchange for Your Privacy.
November 30, 2007
Site that Helps You Identify Tunes by Humming
Still in beta. I tried it on something obscure; it kinda worked but obviously needs more users to help build up its database. It was fun hearing all the goofy hummings from other users around the world, though.
Warning: this is definitely another one of those sites I warned you about here; plus, you have to give it access to your computer microphone, plus since my mic is part of my camera, I had to give it access to my camera. However, at least for now, you don't have to register in order to search by humming.
November 8, 2007
AT&T Whistleblower: Telecoms Do Not Deserve Immunity
Former AT&T technician Mark Klein says that, at the U.S. government's request, AT&T has installed numerous, massive facilities that have been indiscriminately copying all internet traffic, even that of users who are not AT&T customers but whose communications were routed through AT&T's system. As he states in this video, “These installations only make sense if they’re doing a huge, massive domestic dragnet on all internet traffic in the United States.” He also says the telcos are intimately familiar with the constitutional issues from having dealt with warrants for wiretapping, etc., and knew full well that the government's program was in gross violation of the rights of millions of U.S. citizens. (My summary includes some details from an interview with Klein aired yesterday on NPR.)
October 16, 2007
Ongoing, Warrantless Telephone & Internet Surveillance of Us All
Even Starbucks is now required to help them spy on us.
Check out the summaries here and here. Note the post in the first thread indicating that telcos may now be routinely routing ALL communications through jurisdictions outside the U.S., so all can be captured.
All info is good info – until it's used against you for bad purposes. The gummint surveilled John Lennon (Wikipedia) and Martin Luther King (Wikipedia) in its efforts to end their activism, probably succeeding in the case of Lennon, who faced deportation for marijuana use.
A balance of power requires a balance of knowledge: we need to know at least as much about what our gummint is doing as it knows about us. We don't.





.jpg)



.jpg)

.jpg)

.jpg)
