 "Wozniak didn't offer much in the way of specifics . . . . [but said, 't]he more we transfer everything onto the web, onto the cloud, the less we're going to have control over it.'" Steve Wozniak was the inventor of the Apple I and Apple II computers.
"Wozniak didn't offer much in the way of specifics . . . . [but said, 't]he more we transfer everything onto the web, onto the cloud, the less we're going to have control over it.'" Steve Wozniak was the inventor of the Apple I and Apple II computers.
More at Business Insider. You can find more re- the kinds of problems I worry about by clicking on the label, "Worldbeam," at the bottom of this post.
August 6, 2012
Wozniak: Cloud Computing Will Cause "Horrible Problems"
June 18, 2012
Google: Censorship Requests "Alarming"
Per HuffPo:
Google has received more than 1,000 requests from authorities to take down content from its search results or YouTube video in the last six months of 2011, the company said on Monday, denouncing what it said was an alarming trend.(Emphasis supplied; more at the link.) It's even more alarming that it's reached the point that even Google finds it alarming.
* * * * *
Many of those requests targeted political speech, keeping up a trend Google said it has noticed since it started releasing its Transparency Report in 2010.
"It's alarming not only because free expression is at risk, but because some of these requests come from countries you might not suspect — Western democracies not typically associated with censorship," said Chou.
In the second half of last year, Google complied with around 65 percent of court orders and 47 percent of informal requests to remove content, it said.
May 9, 2012
TPP Negotiations in Dallas this Week
 If you liked PIPA and SOPA, you'll probably love the TPP. But only the participating governments and a handful of multinational corporate insiders know for sure, since the negotiations have been conducted in secret – secret, that is, from the public, though not from the corporate insiders who are basically writing the treaty. Thirty-two legal academics from participating countries have written to protest the shut-out; see here. And Occupiers and others have planned a rally and other actions; see, e.g., here.
If you liked PIPA and SOPA, you'll probably love the TPP. But only the participating governments and a handful of multinational corporate insiders know for sure, since the negotiations have been conducted in secret – secret, that is, from the public, though not from the corporate insiders who are basically writing the treaty. Thirty-two legal academics from participating countries have written to protest the shut-out; see here. And Occupiers and others have planned a rally and other actions; see, e.g., here.
Meanwhile, here's an educated guess about what just a few of the proposed treaty's provisions probably include (from Public Knowledge):
- Criminalizing Small Scale Copyright Infringement. Under the TPP, downloading music could be considered a crime. Your computer could be seized as a device that aids this offense and your kid could be sent to jail for downloading. Some of these rules are part of US law. The TPP makes them worse and also imposes similar rules on other countries that don’t have them.
- Kicking People Off the Internet. The TPP would encourage your ISP and the content industry to agree to institute measures such as three strikes—which kicks you off your internet connection after three accusations of copyright infringement—and deep-packet-inspection—which is akin to the USPS opening your mail. While we can not be sure exactly what is in the TPP, these examples are derived from a copy of the TPP’s IP chapter that leaked in February last year, the provisions that were reported to be part of earlier drafts of ACTA, and previous free trade agreements that the US has signed.
- Protecting Incidental Copies. The TPP would provide copyright owners power over “buffer copies.” These are the small copies that computers need to make in the process moving data around. With buffer copy protection the number of transactions for which you would need a license from the copyright owner would increase a great deal. One impact of this could be that the music you stream from services such as Pandora could get much more expensive when rights holders demand higher license fees to compensate them for the “additional” copies.
- Locking out the Deaf and Blind. The TPP would prevent the blind from reading DRM protected ebooks and the deaf from inserting closed captioning onto DRM protected DVDs. In the US, the Copyright Office has made rules in the past that allows the blind to break this DRM. But the continuation of these rules is not a guarantee. And the other TPP countries could fail to make similar rules.
As Zachary, OWS-NY librarian put it, "[p]owerlessness is what happens when you sit behind your desk and do nothing. Powerlessness is signing an online petition, or commenting on an article, or forwarding an e-mail."
April 16, 2012
May 1st: General Strike
April 8, 2012
Occupiers & Others Preparing for General Strike May 1; Noam Chomsky Endorses 99% Spring
 Back in the 70's, experts believed that the improvements possible through technology would increase worker productivity to the point that the 40-hour work week would inevitably shrink to 35 or less, and that we'd all have more leisure while enjoying the same or a better standard of living.
Back in the 70's, experts believed that the improvements possible through technology would increase worker productivity to the point that the 40-hour work week would inevitably shrink to 35 or less, and that we'd all have more leisure while enjoying the same or a better standard of living.
Part of that prediction came true: worker productivity in the U.S has exploded since then. Yet instead of having more leisure and greater wealth, our inflation-adjusted incomes have actually dropped, even while our work week has increased to 50 hours and more, and even though, in most families now, both parents work.
What happened? If you read this blog, you already have an idea (e.g., see here or here).
May 1, a holiday in many countries, is the annual commemoration of the 1886 Haymarket Massacre in Chicago, when Chicago police fired on workers during a General Strike for the eight-hour workday. Now, OWS, Occupy Los Angeles, Occupy Chicago, Occupy Oakland, other General Assemblies, Labor organizers, immigrants’ rights groups, artists, faith leaders, and others are preparing for a General Strike on May 1, calling for all of us to take the day away from school and the workplace, to show that we will not continue to accept corporate and governmental systems that exploit the many in order to enrich the few.
More info on the May 1 General Strike here and here.
"99% Spring" is a congruent but separate effort – see my previous post here; more here, here, and here – which has now been endorsed by Noam Chomsky:
February 29, 2012
What the Stratfor Emails Reveal Re- Efforts Against Wikileaks & Assange
 Per Raw Story,
Per Raw Story,
In an email published by WikiLeaks on Tuesday morning, Stratfor vice president Fred Burton writes that his firm has “a sealed indictment on Assange” . . . . In another email, Burton suggests that authorities could “lock him up” by having Assange detained as a material witness. [c-Blog note: the US Dept. of Justice has refused to confirm whether such an indictment has been issued; some have speculated it's because extradition proceedings are still ongoing in the UK, where the law might bar extradition if it were shown that Sweden is likely to permit extradition to a country {the US} where Assange could face capital punishment.](Emphasis supplied.) More at Raw Story.
Burton’s email was sent in response to a discussion about reports that U.S. prosecutors have not been able to hang the case against Pvt. Bradley Manning on any direct contact with Assange [c-Blog note: which would be required in order to show that Assange had violated US law].
* * * * *
Other Stratfor emails that discuss WikiLeaks hint that sexual assault allegations against Assange might not be entirely legitimate. One message shows Stratfor President George Friedman . . . replying to analyst Chris Farnham, who openly questioned the veracity of the charges and alleged that a “close family friend in Sweden who knows the girl that is pressing charges” against the WikiLeaks founder allegedly said “there is absolutely nothing behind it” aside from a pair of eager prosecutors.
Dead Drops
 "‘Dead Drops’ is an anonymous, offline, peer to peer file-sharing network in public space. USB flash drives are embedded into walls, buildings and curbs accessable to anybody in public space. Everyone is invited to drop or find files on a dead drop. Plug your laptop to a wall, house or pole to share your favorite files and data. Each dead drop is installed empty except a readme.txt file explaining the project. ‘Dead Drops’ is open to participation. If you want to install a dead drop in your city/neighborhood follow the ‘how to’ instructions and submit the location and pictures."
"‘Dead Drops’ is an anonymous, offline, peer to peer file-sharing network in public space. USB flash drives are embedded into walls, buildings and curbs accessable to anybody in public space. Everyone is invited to drop or find files on a dead drop. Plug your laptop to a wall, house or pole to share your favorite files and data. Each dead drop is installed empty except a readme.txt file explaining the project. ‘Dead Drops’ is open to participation. If you want to install a dead drop in your city/neighborhood follow the ‘how to’ instructions and submit the location and pictures."
By Aram Bartholl; see deaddrops.com for more, including how to install.
February 28, 2012
If You Wish to Avoid the Dept. of Homeland Security's Attention
. . . you should minimize your use of the hundreds of terms listed at Animal on social media sites (or elsewhere online?) I was going to list some of them for you so you could see how ridiculous many of them are, but I prefer to avoid the DHS's attentions – although just mentioning them may be all it takes. (But really, terrorists might be planning a tornado?)
February 5, 2012
Rebecca Mackinnon: Consent of the Networked
If you don't read her book, at least watch this:
(Another irresistible re-blog from Boing Boing).
January 31, 2012
More Re- the Infowar
Don't miss Michael Hasting's excellent, recent interview of Julian Assange in Rolling Stone.
Assange mentions the speaker in the video below, Jacob Appelbaum, ("[t]he Tor Project, which protects people around the world from being spied on or censored, lost some $600,000 to the U.S. government, as a result of one of their people, Jacob Appelbaum, having filled in for me once at a conference in New York.") If you haven't seen much of Appelbaum before, his presentation's also not to be missed (you can skip the first 2 min.):
Assange's appeal of extradiction proceedings in the U.K. is due to be heard by the nation's supreme court tomorrow.
January 22, 2012
Clay Shirky on PIPA and SOPA
 Excellent overview of where these bills are coming from and what we should expect going forward, at TED.
Excellent overview of where these bills are coming from and what we should expect going forward, at TED.
July 20, 2011
Feds Indict Coder/Activist for Downloading Too Many Academic Articles (Infowar - Round 2?)
 Per TPM, "coder turned activist" Aaron Swartz has been arrested and charged with "breaking into MIT's network and using an automated program to download more than four million articles from JSTOR, an online database of academic journals maintained at MIT between late September 2010 and early January 2011."
Per TPM, "coder turned activist" Aaron Swartz has been arrested and charged with "breaking into MIT's network and using an automated program to download more than four million articles from JSTOR, an online database of academic journals maintained at MIT between late September 2010 and early January 2011."
Swartz is the former executive director and founder of Demand Progress and co-founder of Bold Progressives, two orgs whose efforts I support, f.w.i.w. TPM also describes Swartz as a prodigy who "has been involved in building many aspects of the web that everyone uses on a daily basis, and concludes:
Demand Progress' Executive Director David Segal professed puzzlement at the Tuesday development. "This makes no sense," he said on the group's blog "it's like trying to put someone in jail for allegedly checking too many books out of the library."(Emphasis supplied.) More at TPM (thanks, Donna!) and the Demand Progress blog.
"It's even more strange because JSTOR has settled any claims against Aaron, explained they've suffered no loss or damage, and asked the government not to prosecute," he added.
But this could be a political statement from Swartz, since he's been a long-time activist on copyright issues. As the indictment notes, Swartz is a fellow at Harvard's Center for Ethics, where his mentor Larry Lessig is the director.
The indictment notes that Swartz could have accessed the research there, but chose instead to break into MIT's network.
The implication seems to be that Swartz may have acted in deliberate provocation – possibly to bring to a head the issue of whether information should, per the "Hacker Ethic," be free.
Swartz's act may in fact have been intended as the next salvo in the infowars.
UPDATE: Just got these links: to ask your FB friends to sign on in support or to tweet it.
FURTHER UPDATE: Swartz supporter dumps 18,592 JSTOR docs on Pirate Bay.
A 31-year-old American who says his name is Gregory Maxwell has posted a 32GB file containing 18,592 scientific articles to BitTorrent. In a lengthy statement posted to the Pirate Bay, he says that Tuesday's arrest of onetime Reddit co-owner Aaron Swartz inspired the document release.More at ars technica.
"All too often journals, galleries, and museums are becoming not disseminators of knowledge—as their lofty mission statements suggest—but censors of knowledge, because censoring is the one thing they do better than the Internet does," he wrote.
July 13, 2011
Ideas for Facebook Apps
July 12, 2011
Tales of Hacking, Madness, and Obsession
Amazon.com currently has available four copies of Underground: Tales of Hacking, Madness, and Obsession on the Electronic Frontier by Suelette Dreyfuss (1997). They do not mention that the book was written by Dreyfuss "with research by Julian Assange." The copies are all used paperbacks and are priced from $349.94.
I could be wrong, but I thought I saw a downloadable copy somewhere on the 'net within the last 15 seconds . . . now where was it . . . .
Anyway, below is the long but fascinating video of a 2011-07-15 program with Assange, philosopher Slavoj Žižek, and Amy Goodman of Democracy Now (a somewhat larger version and a full transcript are available here). The venue for the program was cancelled twice because, the hosting organizations explained, the program was "too controversial," so the program ended up at the Frontline Club, well outside of London center; nonetheless, the 2,000 seats were sold out at £25 each.
By the way, the hearing is ongoing on Assange's appeal of the U.K. court order approving his extradition to Sweden; blow-by-blow at The Guardian.
July 6, 2011
The Hacker Ethic
 I've been reading Hackers by Steven Levy (1984, 1994); 25th Anniversary edition here. The book recounts the seminal exploits of a relatively small number of nerds who, during the late 1950s through the early '80s, created the basic architecture of computer cognition and memory that we inhabit today.
I've been reading Hackers by Steven Levy (1984, 1994); 25th Anniversary edition here. The book recounts the seminal exploits of a relatively small number of nerds who, during the late 1950s through the early '80s, created the basic architecture of computer cognition and memory that we inhabit today.
The meaning of the term, "hacker," has been hijacked since Levy's first edition was published. Now, it's used to suggest a cyber-burglar or worse, who steals or vandalizes for her/his personal profit or pleasure.
But originally, the term simply referred to one who creates computer hardware or software. Levy's "hackers" wrote the operating systems and visual interfaces that brought the mammoth, early computers under our recreative as well as productive control and developed the first widely-available personal computers, among other accomplishments.
And as the Amazon "product description" adds, "[t]hey had a shared sense of values, known as 'the hacker ethic,' that still thrives today."
The "hacker ethic":
- Access to computers – and anything that might teach you something about the way the world works – should be unlimited and total.
- All information should be free.
- Mistrust authority; promote decentralization.
- Hackers should be judged by their hacking, not bogus criteria such as degrees, age, race, or position.
- You can create art and beauty on a computer.
- Computers can change your life for the better.
(See Hackers by Steven Levy, p. 34 {2010 O'Reilly Media, Kindle Edition}.)
For years, these hackers worked day and night, driven by the sheer joy of creating something really cool, and receiving little or nothing more for their efforts beyond the respect of their few, similarly-obsessed fellows. They freely shared the programs and equipment they created, each helping the others to improve and de-bug their creations. As far as they were concerned, none of it should be owned, so none of it could be stolen.
The hackers inhabited a sort of cyber-utopian anarchy in which the only abuse that occurred consisted in the wrong-headed efforts of bureaucrats to restrict access based on claims such as a need for "security." And it was the hacker ethic that made possible the incredible flowering of human potential that occurred during this first decade or two leading up to the commercial success of personal computers and p.c.-based video games.
For me, the fact that such a benevolent anarchy can and has in fact endured for an extended period was one of many interesting revelations afforded by this book. It also provides what seems to be a conscientiously compiled history of our subsequent fall from this Eden, as well as a wealth of details about key, individual hackers and their deeds.
I read the paperback and then bought the e-book; recommended as an invaluable resource.
I recently came across an interesting site, datalove, propounding similar principles:
Data is essentialDatalove appears to be affiliated with Telecomix, one of the Anonymous-type organizations involved in efforts to help Egyptian protesters circumvent Mubarek's shut-down of the Egyptian internet.
Data must flow
Data must be used
Data is neither good nor bad
There is no illegal data
Data is free
Data cannot be owned
No man, machine or system shall interrupt the flow of data
Locking data is a crime against datanity
Love data
One of the nerds described in Levy's Hackers was John Conway, who created the computer game of Life, in which the goal is to design simple, graphic life-forms and then observe how their community either dies out or achieves immortality; below are gifs showing two "immortal" results from this game: (1) a single Gosper's Glider Gun creating "gliders" and (2) a breeder that leaves glider guns in its wake:
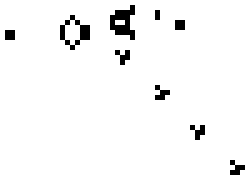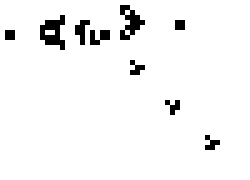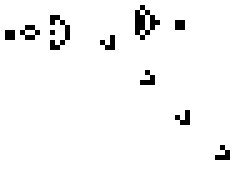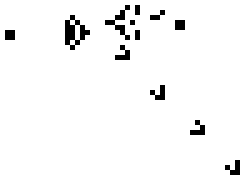
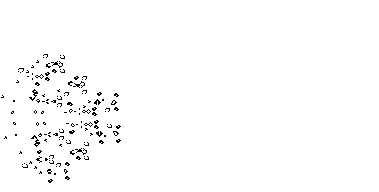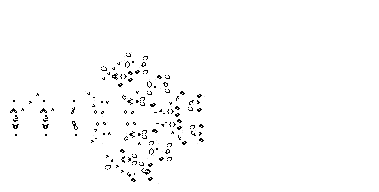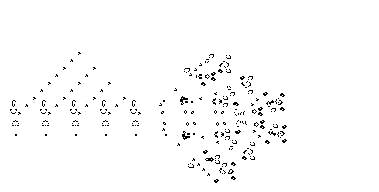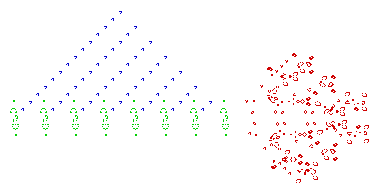
June 24, 2011
Telecomix and We Rebuild
Telecomix seems perhaps to be a subset of We Rebuild, or a term associated with certain news and other functions? Among other efforts, Telecomix worked to provide alternate communication channels during the Mubarek regime's shut-down of Egyptian internet access (see Egypt/Main Page).
We Rebuild describes itself:
We Rebuild is a decentralized cluster of net activists who have joined forces to collaborate on issues concerning access to a free Internet without intrusive surveillance. . . . There are no leaders, nor members. We Rebuild is simply an international chaotic event, and our actions can not be predicted in detail. We are a flow of passions, and we sometimes refer to our driving force as “data-love”.
. . . . The We Rebuild initiative promotes and participates in building the Internet to be accessible for everyone everywhere, enabling true freedom of speech. This is something which can not be guaranteed by states or corporations, but requires the polyvocal voice of the Internet. You will run in to us when you least expect it, especially if you are making decisions about the Internet. But since our strategies are based in the passionate sharing of ideas, you will most likely be happy to see us.
More at the WeRebuild wiki and the Telecomix News Agency; see also Datalove.
May 27, 2011
Why We Need Net Neutrality: ISP's Are Already Throttling the Internet
 If you had any remaining doubt as to whether and how much this is happening, wonder no more. Two projects have shown that Comcast and Road Runner consistently engage in substantial, discriminatory slowing or throttling of internet traffic (euphemistically referred to as "shaping") both to and from users, and that "Comcast, Road Runner (from Time Warner Cable), and Cox all use downstream shaping." (More at Boing Boing)
If you had any remaining doubt as to whether and how much this is happening, wonder no more. Two projects have shown that Comcast and Road Runner consistently engage in substantial, discriminatory slowing or throttling of internet traffic (euphemistically referred to as "shaping") both to and from users, and that "Comcast, Road Runner (from Time Warner Cable), and Cox all use downstream shaping." (More at Boing Boing) They claim they only do it to help manage traffic volumes. But there are many examples of known, wrongful censorship of political or other content, within as well as outside the U.S.; see, e.g., here (Comcast and/or Symantec blocked all e-mails containing URL of site calling for investigation into whether Pres. Bush committed impeachable offenses in connection with the push to invade Iraq, successfully reducing the impact of activists' efforts), here (AT&T censored Pearljam concert by deleting lyrics criticizing Bush), or here (Mindspring and OneNet Communications, successively, blocked site hosting Nuremburg Files).
They claim they only do it to help manage traffic volumes. But there are many examples of known, wrongful censorship of political or other content, within as well as outside the U.S.; see, e.g., here (Comcast and/or Symantec blocked all e-mails containing URL of site calling for investigation into whether Pres. Bush committed impeachable offenses in connection with the push to invade Iraq, successfully reducing the impact of activists' efforts), here (AT&T censored Pearljam concert by deleting lyrics criticizing Bush), or here (Mindspring and OneNet Communications, successively, blocked site hosting Nuremburg Files).
As Lawrence Lessig stated in a recent article, "The innovation commons of the Internet threatens important and powerful pre-Internet interests. During the past five years, those interests have mobilized to launch a counterrevolution that is now having a global impact."
Bad enough that, as "Napoleon said . . . it wasn't necessary to completely suppress the news; it was sufficient to delay the news until it no longer mattered." But worse, ISP's can suppress any info they choose in ways that make it unlikely that many users will ever become aware that anything's been filtered out.
And as stated at sp!ked-IT with reference to Wikileaks, among others, "when an ISP removes [or blocks] content, it invokes the cyber equivalent to the death sentence. When an ISP acts it can effectively destroy a business or censor a political campaign, by making access to that website impossible.
If you agree that protecting the internet as a source of uncensored political information is one of the most urgent issues of our time, please spread the word about it.
May 3, 2011
Recent Assange on Facebook et Al., the Media, War, Etc.
Facebook in particular is the most appalling spying machine that has ever been invented. Here we have the world’s most comprehensive database about people, their relationships, their names, their addresses, their locations and their communications with each other, their relatives, all sitting within the United States, all accessible to US intelligence. Facebook, Google, Yahoo – all these major US organizations have built-in interfaces for US intelligence. It’s not a matter of serving a subpoena. They have an interface that they have developed for US intelligence to use.
Now, is it the case that Facebook is actually run by US intelligence? No, it’s not like that. It’s simply that US intelligence is able to bring to bear legal and political pressure on them. And it’s costly for them to hand out records one by one, so they have automated the process. Everyone should understand that when they add their friends to Facebook, they are doing free work for United States intelligence agencies in building this database for them.
* * * * *
Our No. 1 enemy is ignorance. And I believe that is the No. 1 enemy for everyone – it’s not understanding what actually is going on in the world. It's only when you start to understand that you can make effective decisions and effective plans. Now, the question is, who is promoting ignorance? Well, those organizations that try to keep things secret, and those organizations which distort true information to make it false or misrepresentative. In this latter category, it is bad media.
It really is my opinion that media in general are so bad that we have to question whether the world wouldn't be better off without them altogether. They are so distortive to how the world actually is that the result is . . . we see wars, and we see corrupt governments continue on.
One of the hopeful things that I’ve discovered is that nearly every war that has started in the past 50 years has been a result of media lies. The media could've stopped it if they had searched deep enough; if they hadn't reprinted government propaganda they could've stopped it. But what does that mean? Well, that means that basically populations don't like wars, and populations have to be fooled into wars. Populations don't willingly, with open eyes, go into a war. So if we have a good media environment, then we also have a peaceful environment.
(Emphasis supplied.) More at RT.
February 21, 2011
Solidarity
 Politico reports:
Politico reports:
MADISON, Wis. — Someone in Egypt has been paying attention to what’s happening in Madison and wanted to send a message of solidarity from across the globe — so they ordered pizza.Happy V-Day!
It might seem like a small gesture, but it’s overwhelming to the staff at Ian’s on State Street — a campus staple mere blocks from the Capitol — where in the last few days, they’ve fielded calls from concerned citizens of 12 countries, and 38 out of 50 states looking to donate money to provide free pizza to the Wisconsinites who have congregated here.
February 18, 2011
Alan Dershowitz Advising Assange's UK Attorneys
. . . esp., re- First and Fourth Amendment issues; this is a good thing.





.jpg)



.jpg)

.jpg)

.jpg)
