 I've been reading Hackers by Steven Levy (1984, 1994); 25th Anniversary edition here. The book recounts the seminal exploits of a relatively small number of nerds who, during the late 1950s through the early '80s, created the basic architecture of computer cognition and memory that we inhabit today.
I've been reading Hackers by Steven Levy (1984, 1994); 25th Anniversary edition here. The book recounts the seminal exploits of a relatively small number of nerds who, during the late 1950s through the early '80s, created the basic architecture of computer cognition and memory that we inhabit today.
The meaning of the term, "hacker," has been hijacked since Levy's first edition was published. Now, it's used to suggest a cyber-burglar or worse, who steals or vandalizes for her/his personal profit or pleasure.
But originally, the term simply referred to one who creates computer hardware or software. Levy's "hackers" wrote the operating systems and visual interfaces that brought the mammoth, early computers under our recreative as well as productive control and developed the first widely-available personal computers, among other accomplishments.
And as the Amazon "product description" adds, "[t]hey had a shared sense of values, known as 'the hacker ethic,' that still thrives today."
The "hacker ethic":
- Access to computers – and anything that might teach you something about the way the world works – should be unlimited and total.
- All information should be free.
- Mistrust authority; promote decentralization.
- Hackers should be judged by their hacking, not bogus criteria such as degrees, age, race, or position.
- You can create art and beauty on a computer.
- Computers can change your life for the better.
(See Hackers by Steven Levy, p. 34 {2010 O'Reilly Media, Kindle Edition}.)
For years, these hackers worked day and night, driven by the sheer joy of creating something really cool, and receiving little or nothing more for their efforts beyond the respect of their few, similarly-obsessed fellows. They freely shared the programs and equipment they created, each helping the others to improve and de-bug their creations. As far as they were concerned, none of it should be owned, so none of it could be stolen.
The hackers inhabited a sort of cyber-utopian anarchy in which the only abuse that occurred consisted in the wrong-headed efforts of bureaucrats to restrict access based on claims such as a need for "security." And it was the hacker ethic that made possible the incredible flowering of human potential that occurred during this first decade or two leading up to the commercial success of personal computers and p.c.-based video games.
For me, the fact that such a benevolent anarchy can and has in fact endured for an extended period was one of many interesting revelations afforded by this book. It also provides what seems to be a conscientiously compiled history of our subsequent fall from this Eden, as well as a wealth of details about key, individual hackers and their deeds.
I read the paperback and then bought the e-book; recommended as an invaluable resource.
I recently came across an interesting site, datalove, propounding similar principles:
Data is essentialDatalove appears to be affiliated with Telecomix, one of the Anonymous-type organizations involved in efforts to help Egyptian protesters circumvent Mubarek's shut-down of the Egyptian internet.
Data must flow
Data must be used
Data is neither good nor bad
There is no illegal data
Data is free
Data cannot be owned
No man, machine or system shall interrupt the flow of data
Locking data is a crime against datanity
Love data
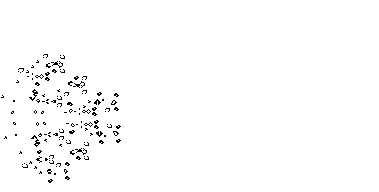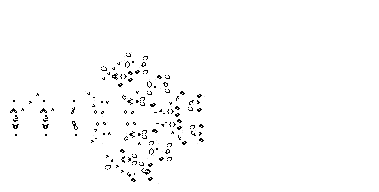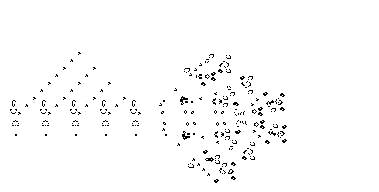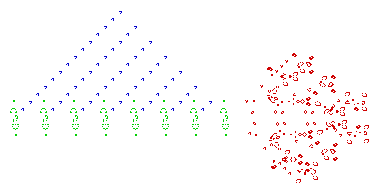
One of the nerds described in Levy's Hackers was John Conway, who created the computer game of Life, in which the goal is to design simple, graphic life-forms and then observe how their community either dies out or achieves immortality; below are gifs showing two "immortal" results from this game: (1) a single Gosper's Glider Gun creating "gliders" and (2) a breeder that leaves glider guns in its wake:
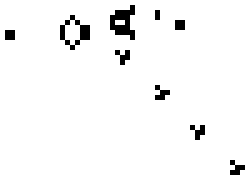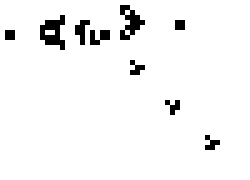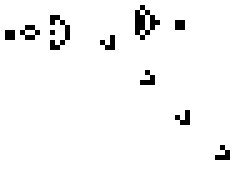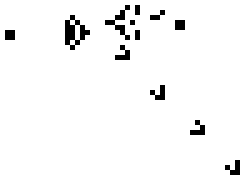






.jpg)



.jpg)

.jpg)

.jpg)
